Protect Yourself from Phishing
-
CSUEB ITS has received a sharp increase in the number of so-called “display name spoofing” email messages. Display name spoofing is the term used for a phishing attempt that tries to convince the email recipient that the message was sent from a trusted individual (often a co-worker or supervisor) even though the attacker does not have direct access to that trusted individual’s account. This technique is especially effective against people using mobile devices to access their email, since mobile email clients display less information about the sender than full desktop clients.
On a desktop client, this is an easy-to-spot phish; the gmail.com address is obvious:
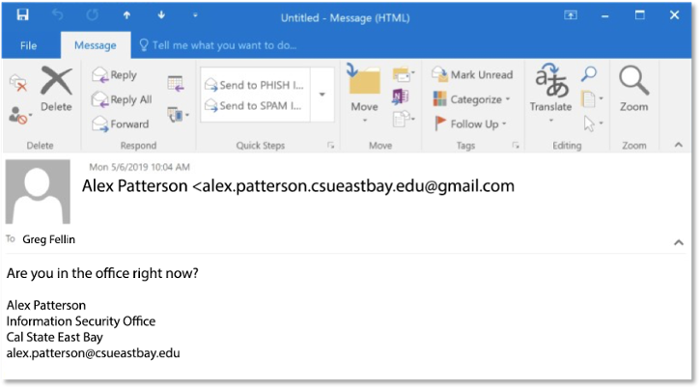
However, compare this with the same email message viewed using Mail for iOS, a common mobile email client:
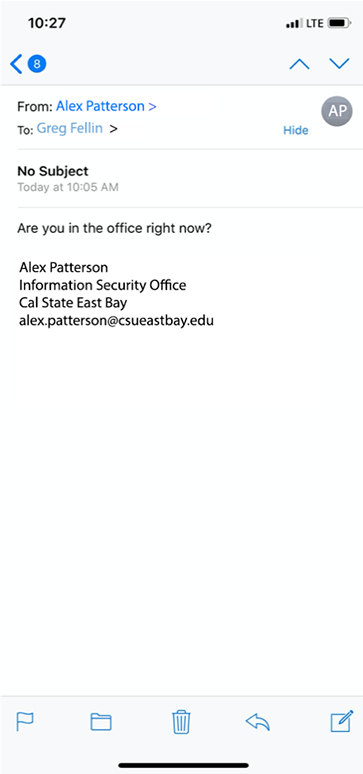
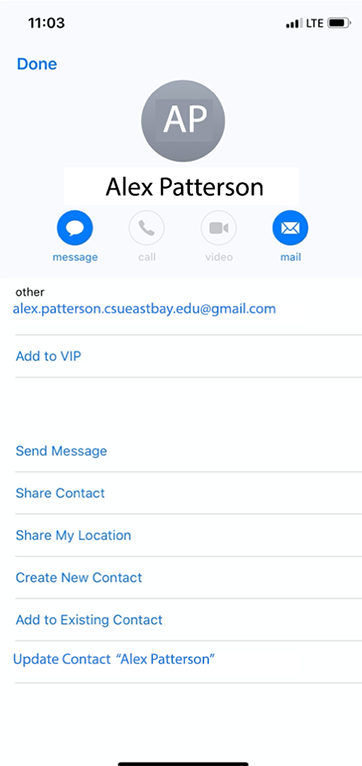
WOW, that is much more convincing! The good news: in Mail for iOS, if you train your users to tap on the “From” name seen in the screenshot on the left, they’ll see the information displayed on the screenshot shown on the right. These steps may differ slightly between individual mobile email clients, but the basic steps to sanity check the sender should be the same.
As you can see below, the process for display name spoofing can be done for anyone, provided the attacker knows the first and last name and username for an individual; this information is publicly available for many department heads from our Online Directory, as well as many of the College webpages.
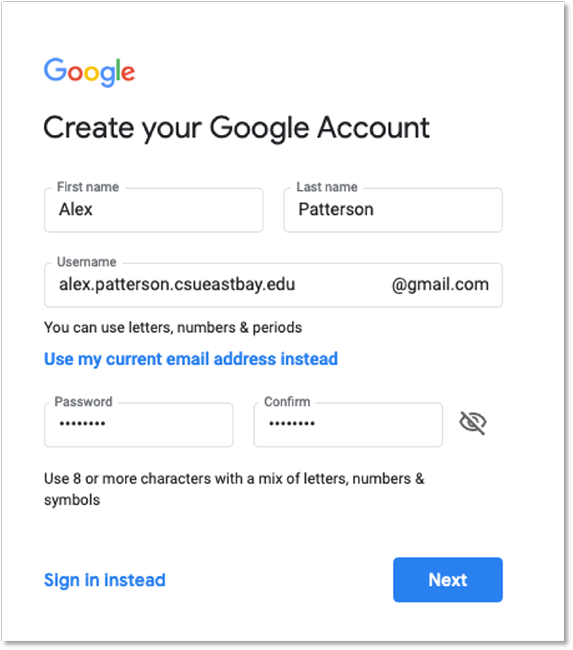
Remember, if you are even slightly suspicious about an email, you can send it to iso@csueastbay.edu and we will be happy to check it out.
-
The following phishing email is attempting to get account credentials from the receiver by having them click a link titled, "Login to Clear History". This link instead goes to a location used by the phisher to collect network credentials from the phishing victim.
-----------------
From: Facebook Accounts <email address not associated with Facebook>
Sent: Tuesday, December 3, 2019 9:28 PM
To: <email address intentionally removed>
Subject: Facebook Account Notice
Dear Customer,
You did not properly sign out during your last facebook session and your facebook session data was left in your browser. As a precaution, we advise that you login with the link below so the facebook session data on your browser can be properly cleared.
Login To Clear History
You are strongly advised to follow instructions to prevent any malicious website from accessing the facebook session data stored in your browser.
Important Security Information:
This authentic message was sent to inform you of security issues detected in one or more of your accounts with us. Kindly adhere to instructions contained herein for continuous use of your facebook accounts.
Replies to this email message will not be read or responded to.
facebook Privacy Operations
Menlo Park, California 94025
20192019 Facebook, Inc.
-
This phishing message was sent from a Canadian domain, and linked to a fake Outlook Web login page. Be on the lookout for any email that may urge you to quickly act with regard to your password, especially if the message is referencing salary or benefits, as they are very often phishing attempts to steal your credentials.
----------------
ALL STAFF ;
This notice is to inform all employee of the current general upgrade of our employee service.This upgrade would help the organization to offer all eligible employee their benefit plan and salary increment that contribute to their overall wellness. These upgrade plans will provide you peace of mind today and years to come. All staff are hereby directed to re-validate their details in order to effect the new salary payment plan, increase in salary and entering of all eligible benefit and promotion. Kindly click on the link NEW PAYROLL SERVICE [redacted] to re-validate your information and also apply for salary increment, promotion and enrollment of entitled benefits.Thank you,
ITS Service Desk.
(C) 2019